(yes… I’ve been happily splitting infinitives since before you were born, most likely)
Some time ago, I wrote this little article when there was a slew of people with hacked Facebook- and Instagram accounts.
It occurred to me that the vast majority of these people made the same mistake: using the same password for different services.
Today, I was reminded of this, so I thought I’d put it up here too.
Here’s how most people get hacked
A hacker will try to get access to a database of, for instance, a web shop. These databases are not always well-protected, so it’s inevitable that he’ll succeed finding a few he can get access to.
If our hacker can get at the table(s) that stores user data, he’ll look for email addresses and passwords.
Some web shops will use a secure way of storing passwords, some won’t. Let’s not bore you with the details, but there is a security algorithm that will make sure not even the database owner can decrypt the password. There are also several security algorithms that will make things a lot harder.
But believe it or not, there are also web shops that will simply store your password as-is, unencrypted.
If our hacker finds one like that, he may want to try breaking into your Facebook/Twitter/online banking account as well, but he can already make good money by selling the data to others, on the dark web or someplace else.
So, let’s suppose you use the same password for Facebook, Gmail or Twitter as you use to access that web shop… this means you’re setting yourself up to have your Facebook, Gmail or Twitter account hacked. Or maybe even all three. Anyone who manages to do that is well on his way to identity theft. Remember, Facebook and Google serve as secure identity providers (the “sign up with Google/Facebook” facility), so if you use that and your account is corrupted, you’re well on your way to becoming well-done toast.
How to figure out if you’re vulnerable
Check your email address
Close any browser you may have open.
Restart your browser
Go to https://haveibeenpwned.com/
DO NOT GO to http://haveibeenpwned.com! The S in https:// is essential!
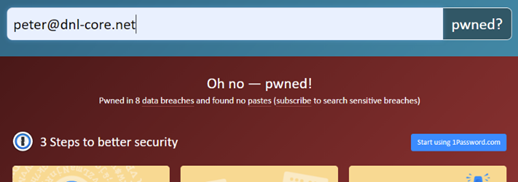
Enter your email address to see if that address appears in the NIST list of exposed email addresses.
If you get the “Oh no — pwned!” message, you may be at risk.
It may well be that your email address shows up, but there’s an old password with it.
Check your password(s)
Close your browser (no need to clear history; no cookies were stored), restart it, and go to https://haveibeenpwned.com/Passwords.
Now type in the password you use to access a service you definitely do not want to be corrupted.
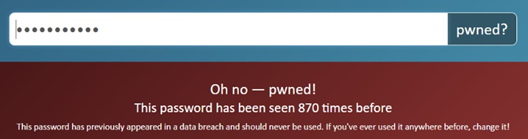
If you get the “Oh no — pwned!” message, you may very well be at risk.
If it says something like “This password has been seen 3,861,493 times before”, this doesn’t necessarily mean that your account has been corrupted 3,861,493 times – it’s just that this password has been used 3,861,493 times.
To give you an idea: at the time I wrote this, I used “password” as the password to be checked, and it turned out to appear in the data-breached passwords database (the NIST database) 3,861,493 times. Which gives you an idea how stupid a substantial number of people are…
Repeat this process for the password for each service you do definitely NOT want to be corrupted. Suggestions:
- Gmail
- Any online banking service
- Paypal
- Your digital identity provider (DigID)
How to decide on a new, better password?
Let’s assume you’re using a common word, say “cauliflower”. At the time of writing, this was used 870 times.
What could we possibly do?
A sensible strategy is to see if we can obfuscate our password with some substitutions.
For instance, we can substitute letters with numbers, or symbols. We could change “cauliflower” to “c@ul1fl0wer”
But anyone who knows cauliflower is your goto vegetable, they will at some point try this. Substituting an a with a @, an o (oh) with a 0 (zero) and an I with a 1 are common practices.
Next step would be to substitute some letters with numbers, but not all of them. That could have us end up at c@ulifl0wer, or c@ul1flower. That’s already a lot better.
Then, we can throw in the odd upper case character: c@ul1floWer.
And the next step is to add a special character, such as a question mark, but not where you’d expect it:
?c@ul1floWer
At the time of writing, this password did not occur in the NIST database. It’ll be interesting to see if it shows up, say, a year from now; that would indicate someone has simply copied it from this document. Don’t ever do that!
Another good strategy is to pick a sentence that is meaningful to you. For instance
“Don’t panic, we’re on the Titanic”
and use only the first letter of each word and all special characters, which would lead to
dp,wott
That password would be too short, but you get the idea. The good news is that it is unlikely to appear in any dictionary, so brute-force hacking (using a dictionary and trying everything) is not going to get a hacker anywhere.
You can spice it up further by adding stuff to it, such as exclamation marks and numbers.
Unfortunately, these passwords are hard to remember. Don’t make the mistake of writing them down and put the slip in your wallet, or under your keyboard – if I were a hacker, those are among the first places I’d look.
So, let’s look at a better strategy.
A third strategy, proposed by Randall Munroe of XKCD fame:
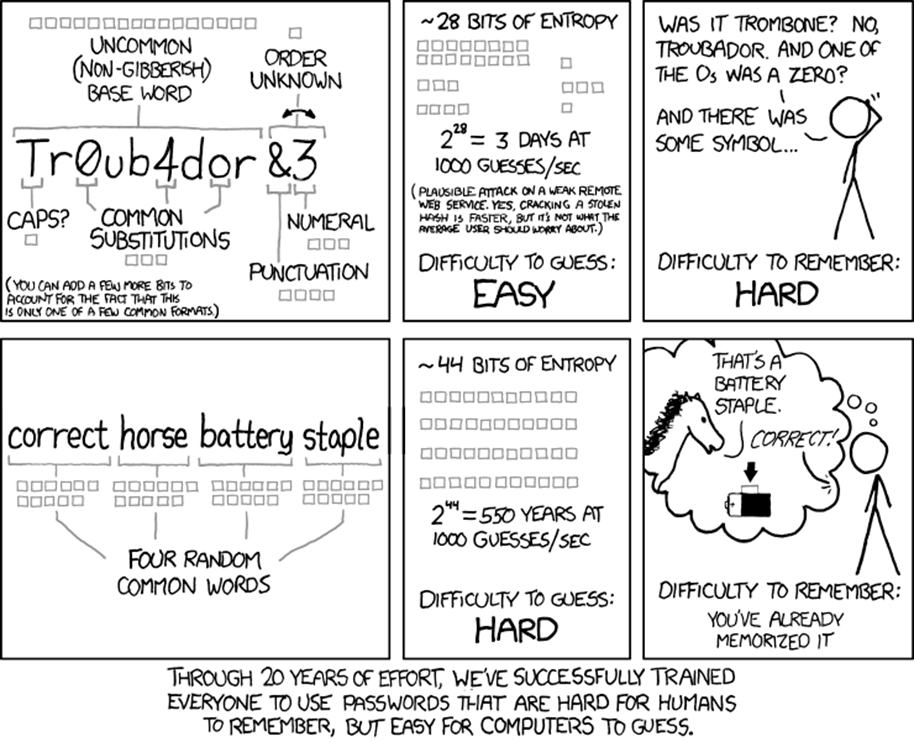
Randall Munroe is an ex-NASA robotics engineer. He’s also one of my heroes. I have nothing to add to Randall’s brilliance.
What I would do is remove the spaces (they have little value), and use a different language, so as to hinder the use of brute-force-using-a-dictionary attack. In fact, that’s what I’ve done, since I’ve mastered a couple languages myself.
If it helps you to remember it, you can draw yourself a picture that explains the password to you, but which would mean nothing to anyone else. But you will probably never need it. I have one here, but it’s so completely meaningless to anyone that even my wife couldn’t figure out what the password was. The password may or may not contain the Polish word for camera, but if it does, my lack of drawing ability makes sure that I’m the only one who will recognize that part of the drawing as a camera.
Oh, the irony
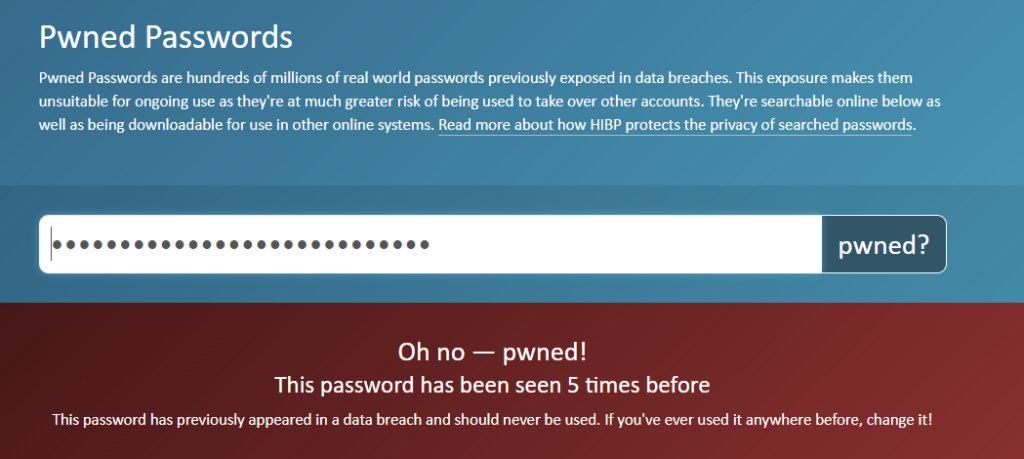
Just for fun, I checked the password “correct horse battery staple”.
What’s the best password strategy?
Be unique
Ideally, you should use a unique password for all the services you’re using. But nobody is going to even try to remember 64 different passwords.
So, without outside help, it’s probably the best idea to choose a unique password for your important services (the ones you won’t want to see hacked!) and ONLY use that password for that one service!
And don’t make it something like ?c@ul1floWerFB for Facebook, because then somebody with average intelligence will already be able to guess your PayPal password (?c@ul1floWerPP). So, think of something else, preferably something I haven’t thought of. But whatever you think of, don’t base any of them on the same ?c@ul1floWer component! Even sticking to a vegetable theme is limiting the possibilities (and thereby improving the guessability) substantially!
The downside of this is that it’ll have you remember many passwords. Most drummers wouldn’t go beyond one, and even bass players would have trouble remembering more than three. 😉
One ring to rule them all
I use a free program called Keepass to store a cartload of passwords. Hundreds of them, all with high entropy, and all are unique.
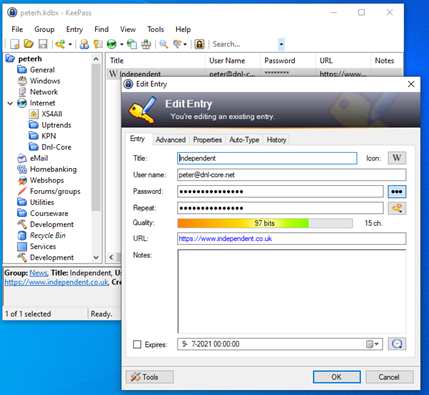
The ONLY password I have to remember is the password to Keepass. That’s a password according to the strategy explained by Randall Munroe hereabove.
The Keepass database (that holds dozens of passwords, most of them randomly generated gibberish, which it will offer to generate for you when you create a new entry) is on a drive in the cloud (Microsoft OneDrive, Google Drive and Dropbox are all proven safe options for cloud storage), so that I can access it from wherever I am. There is also a version for Android, so I can access it on my phone, but only if I take my right hand index or middle finger with me (it’s protected with two of my fingerprints). It’s remarkably easy to use, and it allows me to actually have a unique password for every service and web shop I use without having to remember them.
Questions?
Feel free to launch any questions in the comments!
